
The Evidence
Layer for AI
Walk one training simulation: content safety, AI response, data containment, receipt, audit. GLACIS turns each step into cryptographic evidence—with zero data egress.


The Scenario
A sales rep practices objection handling. Your pharma customer asks…
The platform works. Their legal and risk teams need proof, not assurances:
How do we know our confidential drug data isn't leaking?
Can you prove your content filters actually ran during training sessions?
What evidence can you provide if there's ever a compliance issue?
You answer with documentation and internal logs.
They say "self-maintained records aren't enough."



Blocking Questions
Questions that stall deals
"How do you prove our confidential drug data never leaves your environment or gets used to train your model?" Self-maintained logs aren't sufficient for their risk committee.
"If there's ever a lawsuit, what evidence can you provide that controls actually executed?" Self-maintained logs are contestable. Third-party witnessed proof is not.
Procurement's new bar: Prove execution or don't deploy. Evidence is becoming the default requirement for AI.

The Walkthrough
Receipts on every inference
We attach at inference time via a lightweight sidecar—no code changes required. Hashes stay local, receipts anchor to the witness network. Zero data egress, and every control is provable.
Every inference yields a receipt. Hand it to legal, risk committees, or pharma clients. Evidence becomes the default, not a scramble when a deal is on the line.



Inevitability
Evidence becomes mandatory before 2027
Regulations set the deadline. Litigation and procurement set the bar. Proof shifts from a differentiator to a requirement.
COMPETITIVE ADVANTAGE
Close faster: Answer security questionnaires definitively
Reduce friction: Give governance committees what they need
Differentiate: Your competitors can't prove execution. You can.
Reduce liability: Third-party witnessed proof, not self-maintained logs.
REGULATORY DEADLINES
Standard of care precedes law. NIST AI RMF and ISO 42001 are already the de facto duty of care.
The window: In 18 months, AI training vendors without cryptographic proof will lose pharma deals to those who have it.

The Insight
No one else proves execution
Content guardrails block bad outputs. SOC 2 documents your security posture. Neither proves your controls actually executed on every session.

Infrastructure Players
Cloudflare, AWS, Alinia
Block bad content at runtime
Gap: No compliance mapping. Logs ≠ proof.
GRC Platforms
Vanta, SOC 2
Document policies and procedures
Gap: No content-level enforcement. Trust us.
GLACIS
Cryptographic Attestation
Prove controls executed at inference time
Runtime + Compliance + Proof
Live Demo
Watch controls execute. See receipts stream.
Every AI request gets attested. Third-party witnessed. Zero data egress. Sub-50ms.

Proof Artifacts
Receipts you can show today.
Live at app.glacis.io — verify receipts, inspect witness proofs, and map evidence to governance frameworks.

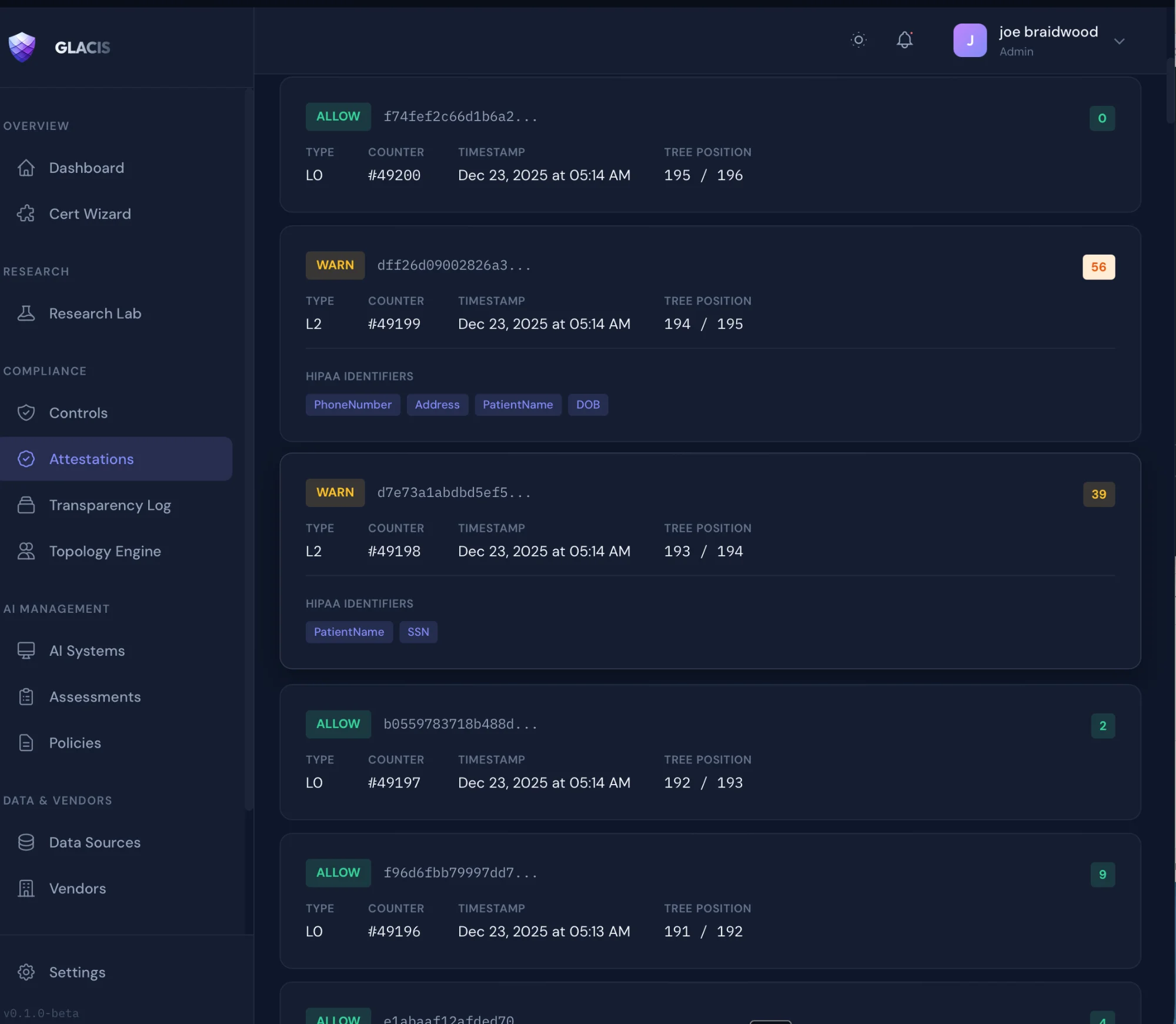
Receipt Timeline
One encounter. Proof chain. Verifiable without PHI exposure.
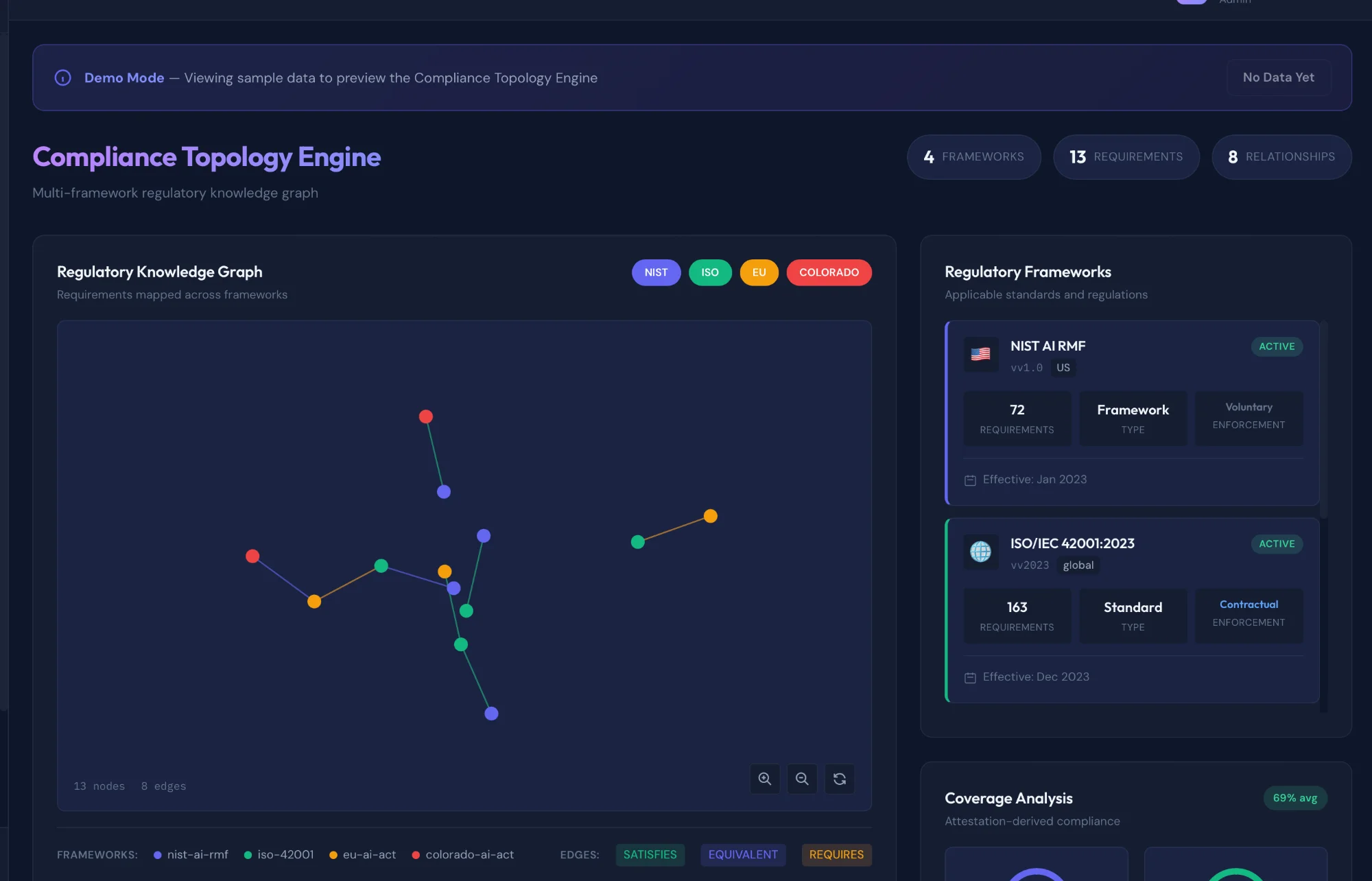
Evidence Mapping
NIST AI RMF • ISO 42001 • EU AI Act • Colorado

70+
Patent claims filed
4 families • Fenwick & West

Defensibility
Building the Category Definition
70+
Patent claims filed
4 families • Fenwick & West
Co-Epoch Attestation
Binds receipts to specific binary versions. Prevents "binary substitution" attacks.
Statistical Safety Signals
Mathematically rigorous sampling for continuous compliance verification.
Zero-Payload Egress
Cryptographic commitments without data exposure. PHI never leaves boundary.
Federated Witness Network
Distributed attestation for independent verification at scale.
Filed Nov 2025 — First-mover advantage in attestation-based AI compliance.
Start a Pilot
Build the evidence layer with us
We are looking for life sciences AI teams ready to prove compliance controls with cryptographic receipts and close pharma deals faster.
DESIGN PARTNERS WE'RE LOOKING FOR
→ AI-powered training or content platforms for pharma
→ Safety controls that need evidence they executed on every session
→ Handling confidential drug data that needs containment proof
→ Selling to pharma companies with compliance review boards


The Evidence Layer for AI
Appendix
Technical Walkthrough
Your Healthcare AI
Gen AI in clinical workflows
GLACIS
SIDECARAttest → Hash → Sign
<50ms • 0 bytes PHI out
Witness Network
Hashes only
Merkle anchor
T+0s Consent captured
The EHR records consent. The sidecar hashes the consent record locally and binds it to the encounter.
T+180ms Inference begins
The model receives prompts. Inputs and outputs are hashed inside the VPC and attached to the receipt.
T+220ms Guardrails executed
Safety checks run inline. The receipt records policy IDs and pass/fail, not the data itself.
T+260ms Receipt issued
A signed receipt is anchored in the witness network and returns immediately to your system.
Any time Audit-ready
Compliance opens the verify link and gets cryptographic proof of execution without PHI exposure.
Zero-Egress = No BAA
No PHI leaves customer boundary. Eliminates months of legal review.
Third-Party Verifiable
Ed25519 signatures + RFC 6962 Merkle trees. Independent verification.
Drop-In Deployment
Lambda layer or container sidecar. Works with any LLM provider.
